
In the early years of the 1970s, the internet was only an idea, an objective that IT specialists couldn’t dream of just yet. Back then, when their highly evolved software suddenly crashed, these engineers and mathematicians referred to these crashes as inconsistencies or instabilities. When these happened, they just reviewed the code, fixed it and rebooted the program. It could take months for them to find and fix the “inconsistencies”, and between those lapses of time when they were trying to fix the problem, life would just go on. without the IT system.
Little did they know back then about the race that was about to commence and the thousands of nightmare-ish hours that future engineers would need to spend fixing these problems in the code that could mean the difference between a big disaster or a partial setback. The beginning of cybersecurity was about to happen.
The first virus: I’m the creeper, catch me if you can!
During the 1970s, the precursor of the Internet was a network called ARPANET. Arpanet run in a rather close and safe testing lab made up with a group of a few American universities. It served mainly for sharing information between high profile people working for those institutions. Arpanet was archaic and slow, sometimes bringing more problems than solutions.
One day, due to a scheduled maintenance, the network was shut down completely, What was going to happen next was totally unexpected. When they turned it back on, a message was displayed on their DEC PDP-10 computers screens saying: “I’m the creeper, catch me if you can!” A software called the Creeper, was producing a message that replicated itself within the network, infecting all other computers. It also erased all previous info and froze the systems. The creeper became widely famous, as the very first computer virus ever. Its maker, was an engineer named Bob Thomas that tried to create “an experimental self-duplicating program that was intended not to inflict damage on, but to illustrate a mobile application.” Now, Bob Thomas is most commonly known as the father of the computer Virus.
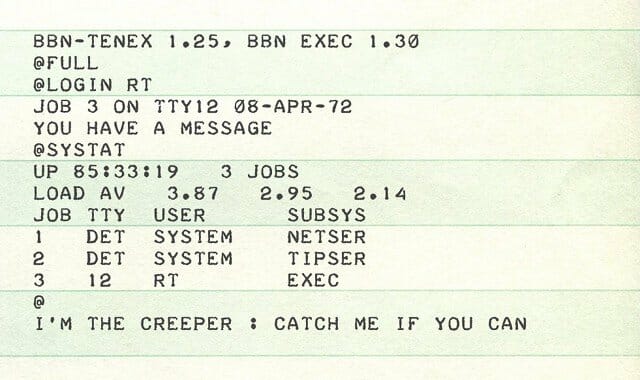
To solve this mess, IT engineers had to come up with innovative software that would be able to target a specific program and remove it from the computer. This saw the birth of “Reaper”, a computer tool designed that became the first antivirus program ever created.
Since then, a kind of race began between programmers and hackers that still goes on. Programmers try to spot vulnerabilities in a system and fix them beforehand, whereas hackers want to exploit vulnerabilities and cause further harm.
The Morris Worm
The vastness and potential destructibility of viruses reached new heights when the internet finally took off in the late 80s, becoming fully widespread with more and more institutions involved and interconnected – healthcare, national administrations, governments, banks, home users, etc.
Another engineer, Robert Tappan Morris decided to measure how deep was the web, by releasing across the internet his last creation: a worm-like software. This was a very special software, as it was the very first worm virus ever created, called The Morris Worm. It operated in the following way: when it would find a critical error in the computer system, it morphed into a virus which replicated rapidly and began infecting other computers resulting in a denial of service. Robert Morris defended himself saying that he meant no harm at all, with “his invention”. Actually, Morris not only invented the very first worm ever, but he also discovered a new type of security breach: the DoS attack.

A DoS attack, or a denial-of-service attack, floods systems, servers or networks, with traffic to exhaust resources and bandwidth. As a result, the system is unable to fulfill legitimate requests. Attackers can also use multiple compromised devices to launch this attack, which is now more common amongst hackers and is called distributed-denial-of-service (DDoS) attack.
Vulnerabilities and exposed back-doors in computing can come in many sizes and shapes, even in systems apparently tough to crack. A great example of this occurred in 1995, when LA based Kevin Poulsen, one of the best black hat hackers of all times, hacked Los Angeles phone system in a bid to win a Ferrari on a radio competition. Poulsen guaranteed his success as he took control of the phone network and effectively blocked incoming calls to the radio station’s number. This was one of the first times that an individual working solo could harm and disrupt an entire network.
The Dawn of Phishing
Around the mid-1990s, what we now call phishing, saw the daylight for the very first time. In 1994, Windows was already a widespread OS used by personal computers sitting on a desk, in almost every home in the US. Microsoft Windows OS was a blossoming industry worth billions of dollars. The competition was fierce among online providers but America Online (AOL) was undoubtedly on the lead, with most users connected to the web and other online services through AOL servers.
Hackers saw the opportunity here and a 17-year-old student of Pittsburgh, PA, known online as “Da Chronic” developed an application mainly used by hackers called AOHell to simplify cracking, by using the extended AOL network. The toolkit contained a new DLL for the AOL client, a credit card number generator, email bomber, IM bomber, Punter, and a basic set of instructions.

More worryingly, the program included a function for stealing the passwords of America Online users. It became a popular toolkit for hackers in the mid-90s, and its software was complex enough to disguise itself among the computer while “working” on the background by stealing data indiscriminately. The first version of the program was released in 1994 by hackers known as The Rizzer.
Other examples of virus attacks who have done solid harm to businesses, users, and even governments, are the Melissa virus in 1999 or the Solar Sunrise in 1998. Since then, hackers have been upgrading their tactics in creative and unexpected ways, featuring even more complex stratagems to break through security systems. More importantly, they always seem to be one step ahead of their counterparts. In fact, a new level of complexity in terms of attacks, and also danger was reached in the early 2000s, when the whole internet was attacked.
The worse cybersecurity breach ever to occur though was in 2017 with WannaCry, although that is a tale to be told in another time.
The Future: AI / Blockchain Attacks?
Nowadays (and even more in the future) more and more businesses, governments, and consumers in all corners of the world rely on interconnected digital systems, so any attack on those systems is increasingly dangerous.
On the other hand, new technologies such as blockchain and AI, have been developing at an incredible pace. Cybersecurity, an ever-evolving field in constant need of new and safer solutions, is also developing Intelligent solutions experimenting with the recent technologies of blockchain and AI. These promise to add extra layers of security to the complex digital systems that structure everything in our lives right now.
The other side of the coin is that cybercriminals will also create fully autonomous AI based attacks. The race that began with the invention of the internet, will just continue.

Aghiath Chbib – Established executive with close to 2 decades of proven successes driving business development and Sales across Europe, Middle East, and North Africa. Expert knowledge of cybersecurity, lawful inceptions, digital forensics, blockchain, data protection, data, and voice encryptions, and data center. Detail-oriented, diplomatic, highly-ethical thought leader and change agent equipped with the ability to close multi-million-dollar projects allowing for rapid market expansion. Business-minded professional adept at cultivating and maintaining strategic relationships with senior government officials, business leaders, and stakeholders. Passionate entrepreneur with an extensive professional network comprised of hundreds of customers with access to major security system integrators and resellers.












