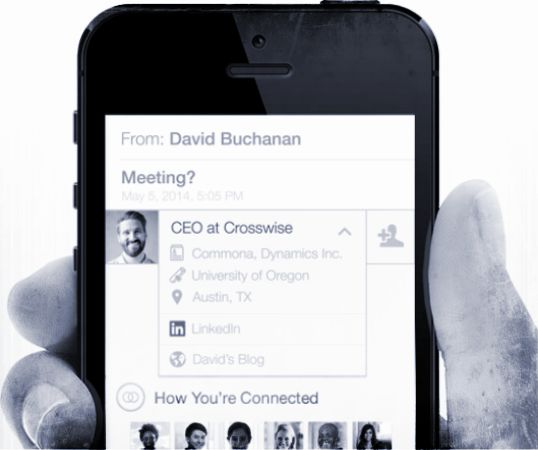
LinkedIn’s mobile Intro tool launched last week Wednesday, has been widely criticized and described as a “lure for phishing hacks”. The new add-on was meant to add and enhance context to emails, but has been rumbled by security experts who say that the plug-in achieves its goals at the expense of user private data. In order to function the app needs a high level of access to user email accounts which naturally introduces a host of privacy and security issues. I don’t think many people are comfortable with the fact that all your emails, must first be served through LinkedIn servers before reaching the end destination.
Security research company Bishop Fox offered the best analysis on the situation:
But that sounds like a man-in-the-middle attack!’ I hear you cry. Yes. Yes it does. Because it is. That’s exactly what it is. And this is a bad thing. If your employees are checking their company email, it’s an especially bad thing.
Bishop Fox lists 10 reasons why intro is potentially a bad idea. They include intro breaking secure email and changing the content of your emails by default. What concerns me is the fact that LinkedIn is prepared to store your email communications.
“It’s metadata, or so they claim. In particular, the list of people with whom you communicated is saved because “If you are not connected with the person on LinkedIn, we may later suggest them as a connection on the LinkedIn website and in our other mobile apps.”
LinkedIn has since responded to the flurry of security concerns. It says that it has examined every scenario a hacker might use to compromise their system. Information security manager Cory Scott, wrote a blog post in order to clear up an address any misconceptions. He said in advance of the launch, LinkedIn isolated intro into a separate network segment and implemented a tight security perimeter across trust boundaries. They also performed hardening of the externally and internally facing services and reduced exposure to third-party monitoring services and tracking.
Cory Scott clearly took particular issue with the assertions made by Bishop Fox. Addressing this directly Scott refuted the claims and said that its profile will only add an email account that communicates with its proxy server. Scott provided links for LinkedIn’s pledge of privacy which was tailored specifically for intro, and also its existing privacy policy which deals with how data is handled in general. The pledge is geared towards building your trust in LinkedIn.
LinkedIn will obviously want to limit any potential damage to the reputation especially amongst business users, who are in fact their bread and butter market. The service is similar to Rapportive, a browser plug-in which I actually use but it functions only in Gmail and Google chrome. Rapportive also predates the NSA revelations, so even though it was purchased by LinkedIn, the company has to be particularly sensitive about the climate that we live in. Indeed the headlines this week will be preoccupied with spying. Graham Cluley offers this advice to those who are still assessing the situation: “LinkedIn wants iPhone users to sign-up for a new service called Intro. My advice? Don’t.”

Hayden Richards is Contributor of IntelligentHQ. He specialises in finance, trading, investment, and technology, with expertise in both buy-side, sell-side. Contributing and advising various global corporations, Hayden is a thought leader, researching on global regulatory subjects, digital, social media strategies and new trends for Businesses, Capital Markets and Financial Services.
Aside from the articles, interviews and content he writes for IntelligentHQ, Hayden is also a content curator for capital markets, analytic platforms and business industry emerging trends. An avid new media explorer Hayden is driven by a passion for business development, innovation, social business, Tech Trading, payments and eCommerce. A native Trinidadian, Hayden is also a veteran, having served with the Royal Air Force Reserves for the past 10 years.
Follow Hayden on Twitter @HaydenARichards, linkedin.com/haydenhrichards and http://www.scoop.it/u/hayden-richards