Are you concerned about how secure your sensitive data really is? Data masking is a vital tool that ensures your organization meets crucial privacy regulations while protecting crucial information.

In this article, we’ll explore effective data masking strategies, address common challenges, and look at emerging trends to help you maintain compliance and safeguard your data. Let’s see how you can enhance your privacy measures.
Critical Role of Data Masking in Privacy Compliance
Data masking plays a crucial role in protecting sensitive information and ensuring compliance with privacy regulations.. It helps conceal the original data, providing a functional but non-sensitive equivalent. Understanding data masking meaning is crucial for effectively implementing it. Let’s explore its key aspects, including how it works, why it’s essential for protecting your data, and the benefits it offers in adhering to strict privacy standards.
Mitigating Privacy Risks
According to a study, the average cost of a data breach in 2023 was $4.45 million, emphasizing the critical need for robust data protection measures such as data masking. Data masking significantly reduces the risk of unauthorized access to sensitive information by obscuring or replacing original data with fictitious but realistic data. By obscuring or replacing original data with fictitious but realistic data, you can protect Personally Identifiable Information (PII) and other sensitive data from potential breaches or misuse.
- Data masking can reduce the risk of data breaches by up to 95% when properly implemented.
- It helps maintain data confidentiality while preserving the format and usability of the information.
For instance, when you mask customer credit card numbers, you replace the actual digits with randomized ones, maintaining the same format but rendering the data useless to potential attackers.
Regulatory Mandates and Data Masking
Data masking directly addresses key requirements of major privacy regulations such as GDPR, HIPAA, and CCPA. By implementing robust data masking practices, you can ensure compliance with these stringent laws.
- GDPR Article 32 mandates the implementation of appropriate technical measures to ensure data security, including pseudonymization and encryption. Companies that fail to comply with GDPR can face fines up to 4% of their annual global turnover or €20 million, whichever is higher.
- HIPAA requires healthcare organizations to implement safeguards that ensure the confidentiality of electronic protected health information (ePHI).
By masking patient data in non-production environments, healthcare providers can comply with HIPAA requirements while still allowing developers to work with realistic data sets.
Implementing Effective Data Masking Strategies
Ensuring privacy compliance through data masking requires implementing effective strategies tailored to your organization’s needs
Techniques and Tools
To effectively mask your data, you need to understand the available techniques and tools. Two primary methods of data masking are:
Static Data Masking: This technique permanently alters data at rest, typically in non-production environments. It’s ideal for creating sanitized copies of databases for testing or development purposes.
Dynamic Data Masking: This method masks data in real-time as it’s being accessed, allowing for more flexible protection. It’s particularly useful in production environments where different users may have varying levels of data access.
Leading tools in the market for data masking include:
- IBM InfoSphere Optim Data Privacy
- Oracle Data Masking and Subsetting
- Informatica Data Masking
These tools offer features like automated sensitive data discovery, customizable masking rules, and integration with major database platforms.
Best Practices for Implementation
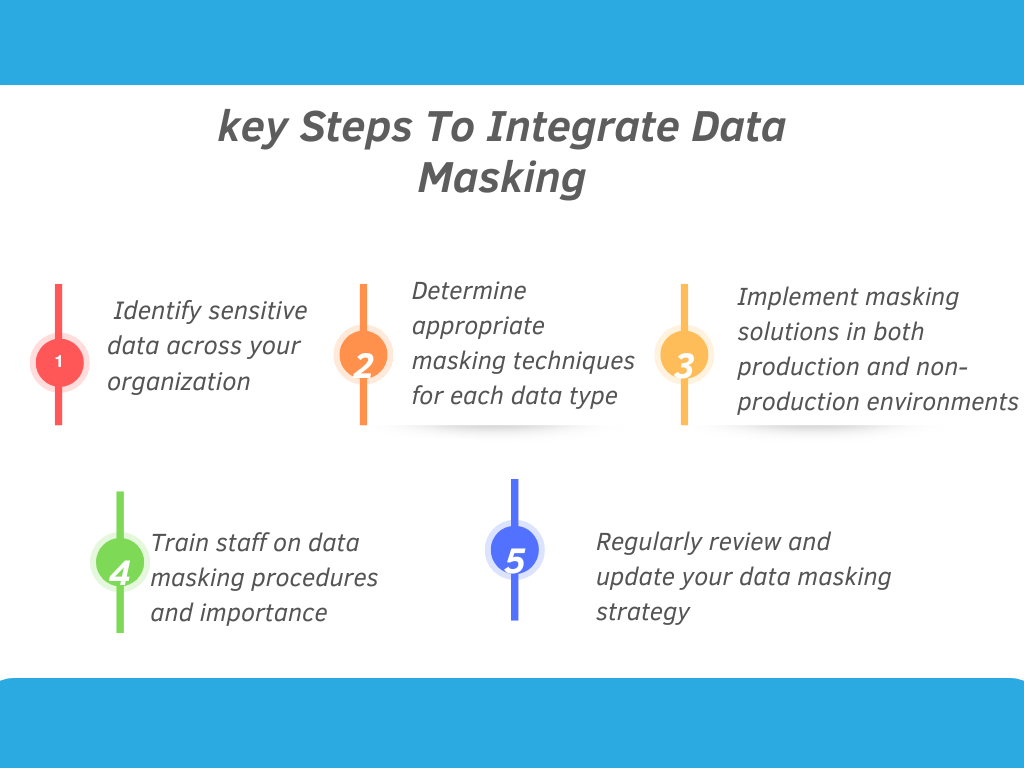
To successfully integrate data masking within your existing data management systems, consider these key steps.
When identifying sensitive data, use automated discovery tools to scan your databases and applications. This ensures you don’t overlook any critical information that requires masking.
Ensuring Continuous Compliance Through Data Masking
Implementing data masking is not a one-time task. You need to ensure continuous compliance to maintain data privacy.
Automated Compliance Monitoring
Implementing automated tools for continuous compliance monitoring can significantly enhance your data protection efforts. These solutions can:
- Automatically detect and mask sensitive data in real-time
- Provide alerts for potential compliance violations
- Generate compliance reports for auditing purposes
Using automated monitoring tools allows you to quickly identify and address any gaps in your data masking strategy, ensuring ongoing compliance with privacy regulations
Auditing and Reporting
Regular audits are essential for verifying compliance with data protection regulations. Data masking facilitates accurate and comprehensive reporting by:
- Providing clear audit trails of data access and modifications
- Enabling the creation of masked datasets for compliance testing
- Supporting the generation of detailed reports for regulatory bodies
Implement a regular auditing schedule to review your data masking processes and ensure they remain effective as your data landscape evolves.
Challenges and Solutions in Data Masking
Data masking is crucial for privacy compliance but presents its own set of challenges. Understanding these challenges and their solutions is key to successful implementation.
Overcoming Technical Challenges
While implementing data masking, you may encounter performance issues and data usability concerns. To address these challenges:
- Use efficient masking algorithms to minimize the impact on performance
- Implement column-level security to balance protection and functionality
- Leverage data virtualization techniques to improve masked data accessibility
Consider using format-preserving encryption for sensitive fields to maintain data usability while ensuring strong protection.
Ensuring Data Integrity
Maintaining data integrity across different environments is crucial. To verify the effectiveness of your data masking techniques:
- Conduct regular data quality assessments
- Implement data validation checks post-masking
- Use data comparison tools to ensure consistency between masked and original datasets
Regularly test your masked data to ensure it remains statistically representative of the original data, allowing for accurate analysis and testing.
Future Trends in Data Masking and Privacy Compliance
As technology and regulations evolve, your approach to data masking and privacy compliance must evolve as well.
Advancements in Data Masking Technologies
Emerging technologies are set to enhance the effectiveness and efficiency of data masking:
- AI-powered data discovery tools for improved sensitive data identification
- Machine learning algorithms for more sophisticated masking techniques
- Blockchain technology for enhanced data integrity and auditability
Stay informed about these advancements and consider how they might be integrated into your data masking strategy to improve your privacy compliance efforts.
Evolving Regulatory Landscape
As privacy laws continue to evolve, your data masking strategies must adapt. Prepare for future compliance requirements by staying informed about upcoming privacy regulations staying informed about upcoming privacy regulations:
- Staying informed about upcoming privacy regulations
- Implementing flexible data masking solutions that can adapt to new requirements
- Fostering a culture of privacy within your organization
Be proactive in anticipating regulatory changes and adjusting your data masking practices accordingly to ensure ongoing compliance.
Wrap Up
Data masking is essential for achieving and maintaining privacy compliance in today’s data-centric world. By implementing robust data masking practices, you can protect sensitive information, meet regulatory requirements, and build trust with your customers and stakeholders.
Take action today to assess and enhance your current data masking strategies. Start by conducting a thorough audit of your sensitive data, evaluating your existing masking techniques, and exploring advanced tools that can streamline your compliance efforts.
Effective data masking is not only about meeting regulatory requirements but also about safeguarding your organization’s most valuable asset: its data. By prioritizing data masking as part of your overall data protection strategy, you’re taking a crucial step towards ensuring long-term privacy compliance and data security.
| Feature | Static Data Masking | Dynamic Data Masking |
| When applied | Before data is stored | Real-time, as data is accessed |
| Permanence | Permanent alteration | Temporary, on-the-fly masking |
| Use case | Non-production environments | Production environments |
| Performance impact | Minimal | Potential slight impact |
| Flexibility | Less flexible | More flexible |
| Implementation complexity | Moderate | Higher |
| Data consistency | Consistent across all users | Can vary based on user access rights |
| Reversibility | Not reversible | Potentially reversible |
FAQs:
- What is the primary purpose of data masking?
Data masking primarily aims to protect sensitive information by replacing it with fictitious but realistic data, thereby ensuring privacy compliance and reducing the risk of data breaches.
- How does data masking differ from encryption?
Data masking replaces sensitive data with realistic, non-sensitive equivalents, while encryption transforms data into an unreadable format that requires a key to decrypt.
- Can data masking affect the usability of my data?
When properly implemented, data masking preserves the format and statistical properties of the original data, maintaining its usability for testing and analysis purposes.

IntelligentHQ Your New Business Network.
IntelligentHQ is a Business network and an expert source for finance, capital markets and intelligence for thousands of global business professionals, startups, and companies.
We exist at the point of intersection between technology, social media, finance and innovation.
IntelligentHQ leverages innovation and scale of social digital technology, analytics, news and distribution to create an unparalleled, full digital medium and social business network spectrum.
IntelligentHQ is working hard, to become a trusted, and indispensable source of business news and analytics, within financial services and its associated supply chains and ecosystems.










