
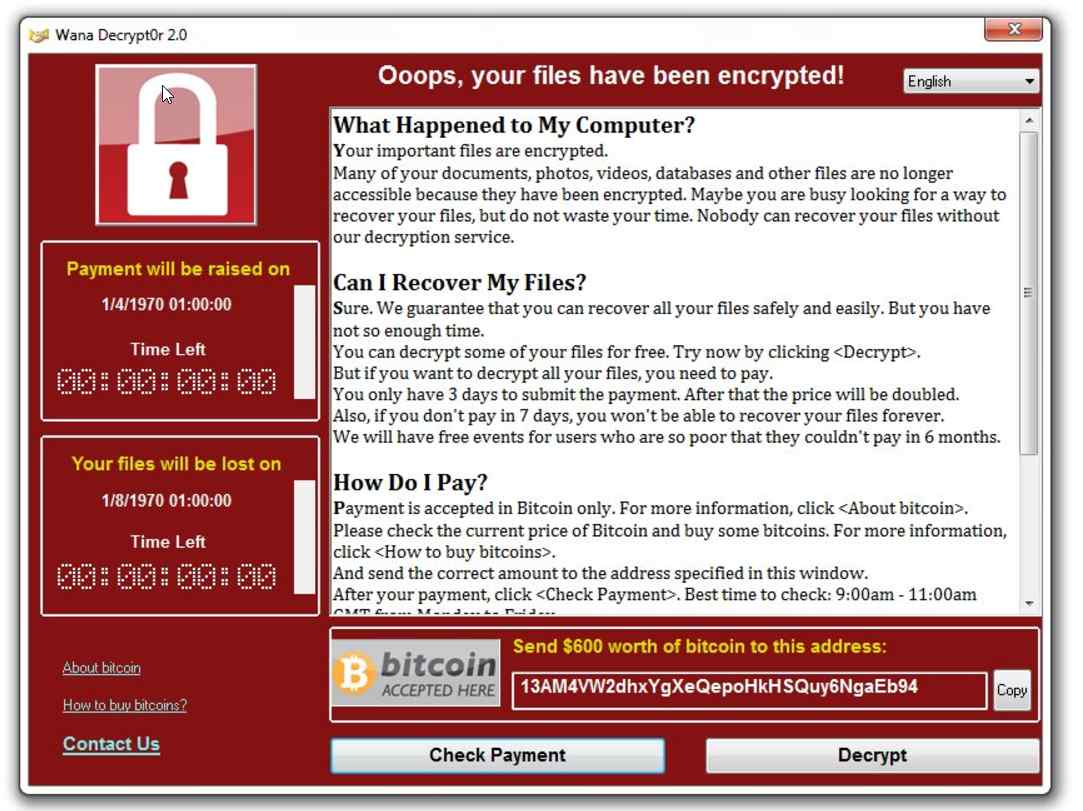
On Friday, 12 May 2017 the NHS in England suffered its worst joint cyber-attack of its history. A ramsonware called WannaCry made its way through thousands of PC across the nation while infecting them in its wake. The worm-type virus was able to encrypt data from at least 603 primary care organisations and affected more than 81 out of 236 NHS belonged Trusts. The attack led to a complete disruption of the service on the 12th, and it took the authorities one more week to fully restore the affected Trusts. A recent investigation found that more than 6,912 appointments had been cancelled, and estimated that over 19,000 appointments would have been cancelled in total.
WannaCry was a ransomware worm that encrypted all the data stored in Windows’ running PCs. Hackers used a back-door exploit in Microsoft’s OS to infect the computers through a code named EternalBlue, secretly developed by the United States National Security Agency. After the attack, cyber-criminals asked Bitcoins in order to liberate kidnapped computers.
It is also known that the EternalBlue code was behind the NotPetya malware attack perpetrated in Ukraine in June 2017. The highly upgraded version of Petya, with worm capabilities this time, infected more than 12,500 computers in Ukraine through the popular accounting tool, M.E.Doc, servers. The virus then spread out to more than 64 other countries infecting thousands of computers. Again, victims were asked to pay $300 in Bitcoins to the hacker’s address.
These two examples are the most commonly known malware attacks made within the last years, but not the only ones. They just represent how vulnerable are today’s organisations, even those at the highest levels. No computer, server, service or host, from whomever it belongs to, it is safe from hackers.
Not even cryptocurrencies are safe
Ethereum, a largely known cryptocurrency that allows participants to create smart contracts between them, was also hit of what is now called as the “crypto-heist”. “At the beginning of July 2017, $7.4 million in Ether was stolen from the Ethereum app platform in a manner of minutes. Then, just weeks later came a $32 million heist. The whole incident raised questions about the security of blockchain-based currencies,” explained it in an article expert Josh Fruhlinger from CSO magazine.
In this latest entry, hackers just took what all criminals in the end want, money, without the need of kidnapping or stealing data from users. However, the means that hackers use to achieve their goals vary from a whole range of creative – and criminal – activities. Distributed Denial of Services in the shape of DDoS attacks; Man-in-the-middle (MitM) attack, when a hacker inserts itself between the communications of a client and a server; Phishing attacks or the practice of sending emails that appear to be from trusted sources with the goal of gaining personal information; or malware attack, in which ransomware, worms or trojans are amongst them, are the most common ones.
Hackers, as the likes of Shadow Brokers, are always seeking back-doors, exploits, faults in software’s code to breach antivirus securities and infect their hosts. The only trend now is that they focus their activity in long-range attacks, aiming directly at governments and big companies. A scary practice with the capability of risking millions of personal and private data.
The Good Hackers
However, not all hackers have greed intentions, there are some out there going after noble causes. These are called the White Hat Hackers, IT specialists “who break into protected systems and networks to test and asses their security. White hat hackers use their skills to improve security by exposing vulnerabilities before malicious hackers (known as black hat hackers) can detect and exploit them. Although the methods used are similar, if not identical, to those employed by malicious hackers, white hat hackers have permission to employ them against the organization that has hired them,” as described by the Techopedia.
These hackers are moved by ethical motives and their activity might be crucial for companies to spot vulnerabilities before the bad guys find them, and the fact that they know how attackers operate often gives them a valuable insight into how to prevent attacks. Charlie Miller might be one of the most famous White Hat Hacker nowadays. He found a bug in Apple’s MacBook Air and its browser, Safari, back in 2008 and, instead of kidnapping and asking for a bounty, he reported it to Apple. In a good gesture, the company rewarded the young man with $15,000 for his good will.
Companies are increasingly relying on hackers and personal experts to work for them. These rewards even come with a double intention: make more attractive to work with companies than trying to exploit them.
“Large companies, particularly tech firms like Facebook, Microsoft and Google, offer a reward to researchers or hackers who discover security holes within their networks or services, a practice known as “bug bounties”. This encourages them to report these holes, allowing them to be fixed before they can be found by criminals,” added ITPro online magazine.
Fighting an Endless Battle
These hackers can avoid a huge amount every year for governments and companies alike. It is said that cyber-crime costs the global economy around $445 billion every year, and the figures keep growing every year that comes by. Efforts aren’t clearly enough and while cyber-crime still shows an easy way of earning money, hackers will be hitting hard.
Companies, governments and citizens need to be aware of potential dangers when utilizing technology, although very little information is given away and tips can be summarised in strong passwords and the need of an antivirus. Users need more than just vague tips and events, conferences, verified info on social media and mass media have to make an extra effort in literate technology users.
Times are changing, and while emerging technologies such blockchain or AI show exponential upgrades in our daily lives, it also represents unprecedented hazards yet to be seen. Hackers, for sure, will try to exploit them; we, on the other side, need to make their lives the hardest we can. The tides need to be turned in this endless fight.

Hernaldo Turrillo is a writer and author specialised in innovation, AI, DLT, SMEs, trading, investing and new trends in technology and business. He has been working for ztudium group since 2017. He is the editor of openbusinesscouncil.org, tradersdna.com, hedgethink.com, and writes regularly for intelligenthq.com, socialmediacouncil.eu. Hernaldo was born in Spain and finally settled in London, United Kingdom, after a few years of personal growth. Hernaldo finished his Journalism bachelor degree in the University of Seville, Spain, and began working as reporter in the newspaper, Europa Sur, writing about Politics and Society. He also worked as community manager and marketing advisor in Los Barrios, Spain. Innovation, technology, politics and economy are his main interests, with special focus on new trends and ethical projects. He enjoys finding himself getting lost in words, explaining what he understands from the world and helping others. Besides a journalist, he is also a thinker and proactive in digital transformation strategies. Knowledge and ideas have no limits.



























