
The SWOT guide to blockchain is a guide in 6 parts, where both the opportunities and challenges of blockchain are considered. Blockchain has the potential to be groundbreaking, offering opportunities and better solutions for a range of situations and industries worldwide. In the fifth part of this guide, we analyze a specific strength of blockchain technology: safety and trust… but we also explain how that strength can be misleading to the common person.
By Maria Fonseca and Paula Newton
Safety and Trust
One of the major benefits that is heavily touted around about blockchain is its safety and the fact that it can be trusted. This is worth exploring in greater detail rather than taking a blinkered and evangelical approach towards the technology. Having one’s head in the sand is risky. On the other hand, fully understanding the technology and any limitations it may have, particularly with regard to trust and safety is beneficial in developing and implementing solutions that are as beneficial as they can possibly be for society, businesses and individual consumers.
How does Blockchain secure data?
Blockchain stores data in a manner that makes it difficult for anyone to change or manipulate later. Through a complex system of mathematics, algorithms and software, blockchain systems are argued to be as secure as they can possibly be. This is important to the overall proposition and key selling point – the fact that data can be shared securely between entities that may not trust one another. However, people are people, and there will always be some who look for ways around such security, seeing it as a challenge, and focusing on the illicit rewards to be gained from doing so.
Blockchains are secure by the fact that ledgers of data are stored in many copies on various computers – considered to be nodes within the network. When a transaction is made and submitted to the ledger, this data is checked against all the nodes. Those responsible for the nodes are “miners” and they are rewarded for their adding of new blocks to the chain. The fact that there is a protocol of agreement between the nodes makes it difficult to manipulate, as is the cryptographic fingerprint (a “hash”) that each block has, and which is unique. Consensus protocol security requires checking that a hash matches its block, and nodes update once this is verified. All blocks have the unique hash of the previous block. This means the ledger must be changed for that block, and every new one, and this must be achieved quicker than new blocks get added – to avoid conflicts and rejections. It is this which makes the blockchain immutable.
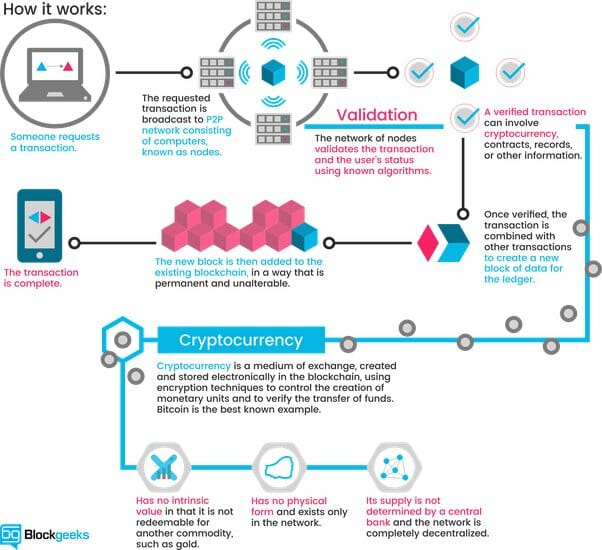
Is Blockchain Really Decentralized?
One characteristic of blockchain that has made it so attractive is “decentralization.” this all pertains to the idea that exact copies of the blockchain are kept on a large and widely distributed network of nodes. Since there is no central point but a network of nodes, all with the same importance, there’s no one weak point to attack. Plus, it’s almost impossible for anyone assesses enough computing power to subvert the network. But this is actually misleading… the reality, according to recent work by a team of academics, from Cornell University, is that neither Bitcoin nor Ethereum is as decentralized as you might think. Their study discovered that the top four bitcoin-mining operations had more than 53 percent of the system’s average mining capacity per week. As for Ethereum, 3 miners accounted for 61 percent.
So there you have it, what seems to be a strength, transformed into weakness.
Can you hack a blockchain system?
As expected, people have already been looking for and finding ways to cheat the system. The same research by academics at Cornell University has shown that blockchains can be subverted, even in the scenario that a person has a lower level than 50% of the mining power of the other minors. It is possible to fool the system to gain an advantage. This means the system is not necessarily as secure as originally thought. Additionally, attacks can be carried out – known as “eclipse attacks”. These occur when the attacker gains control of a node’s communications. Since all nodes need to be communicating all of the time, if the attacker can convince other nodes to accept false data as if it came from the rest of the network, fake transactions could be confirmed. Hackers have also been hacking so-called “hot wallets” where private cryptographic keys are stored. All of this leads to questions about security and trust within blockchain, and solutions need to be found to defend against these types of issues.
The SWOT Guide to Blockchain Part 1
The SWOT Guide to Blockchain Part 2
The SWOT Guide to Blockchain Part 3
The SWOT Guide to Blockchain Part 4
The SWOT Guide to Blockchain Part 5
The SWOT Guide To Blockchain Part 6

Maria Fonseca is the Editor and Infographic Artist for IntelligentHQ. She is also a thought leader writing about social innovation, sharing economy, social business, and the commons. Aside her work for IntelligentHQ, Maria Fonseca is a visual artist and filmmaker that has exhibited widely in international events such as Manifesta 5, Sao Paulo Biennial, Photo Espana, Moderna Museet in Stockholm, Joshibi University and many others. She concluded her PhD on essayistic filmmaking , taken at University of Westminster in London and is preparing her post doc that will explore the links between creativity and the sharing economy.


























